Connecting Ping Identity with Flexopus is possible through the standard SAML2 authentication protocol. Additionally, you can configure the SCIM API for user provisioning.
This article will cover the following instructions:
- What is Ping Identity?
- SAML2 Single Sign On (SSO) configuration between Ping Identity and Flexopus for user authentication
- SCIM API configuration between Ping Identity and Flexopus for user and group provisioning
What is Ping Identity?
Ping Identity provides federated identity management and self-hosted identity access management (IAM) solutions to web identities and single sign-on solutions, being one of a number of organizations competing to provide standards to replace passwords for authenticating to web applications.
Visit the official website for more information: https://www.pingidentity.com/
SAML2 Single Sign On (SSO) configuration between Okta and Flexopus for user authentication
Follow the instructions:
- Select the Connectors menu point.
- Select the Application menu point and click on the add button in the top to create a new application.
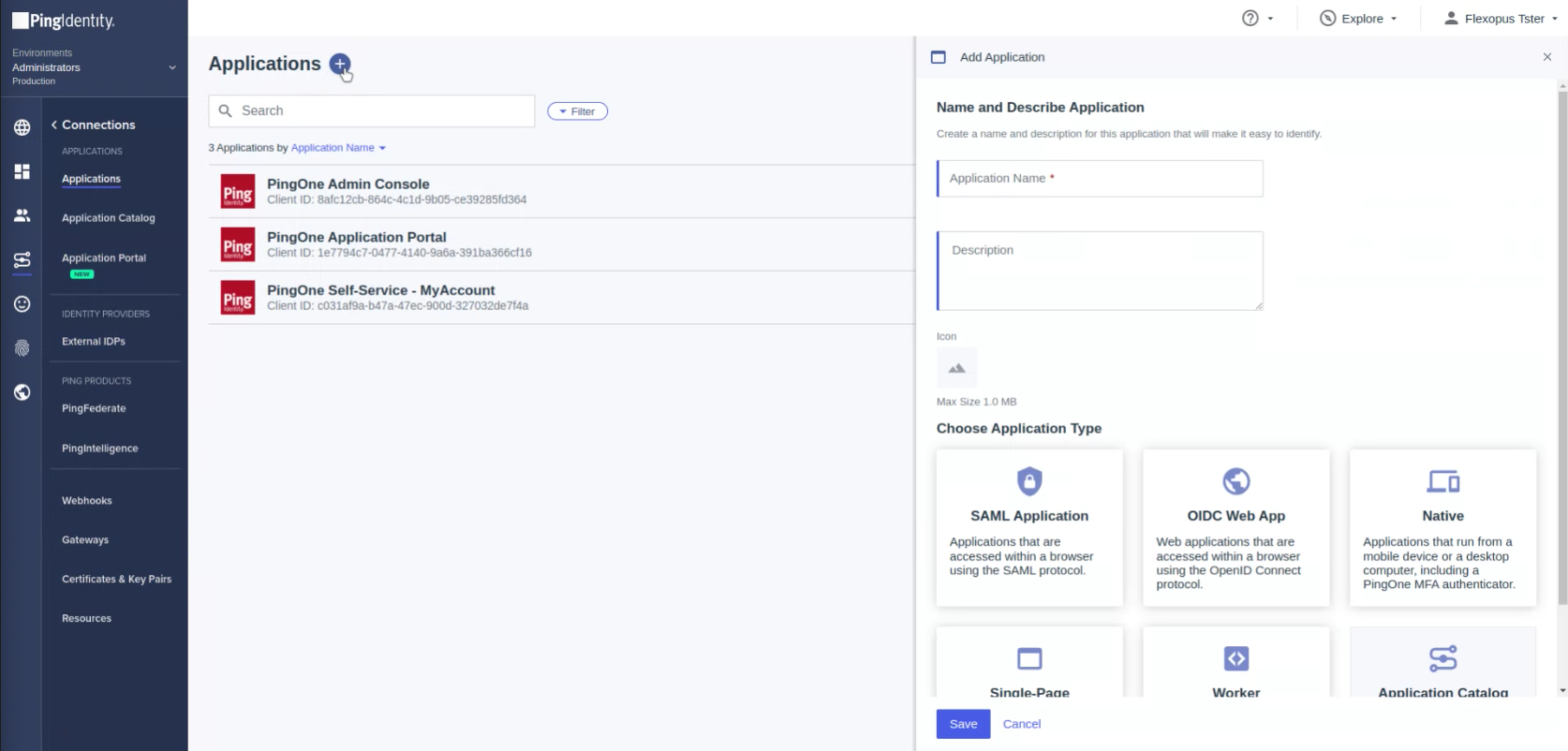
- Name: Flexopus
Description: Desk Sharing Software
Select: SAML Application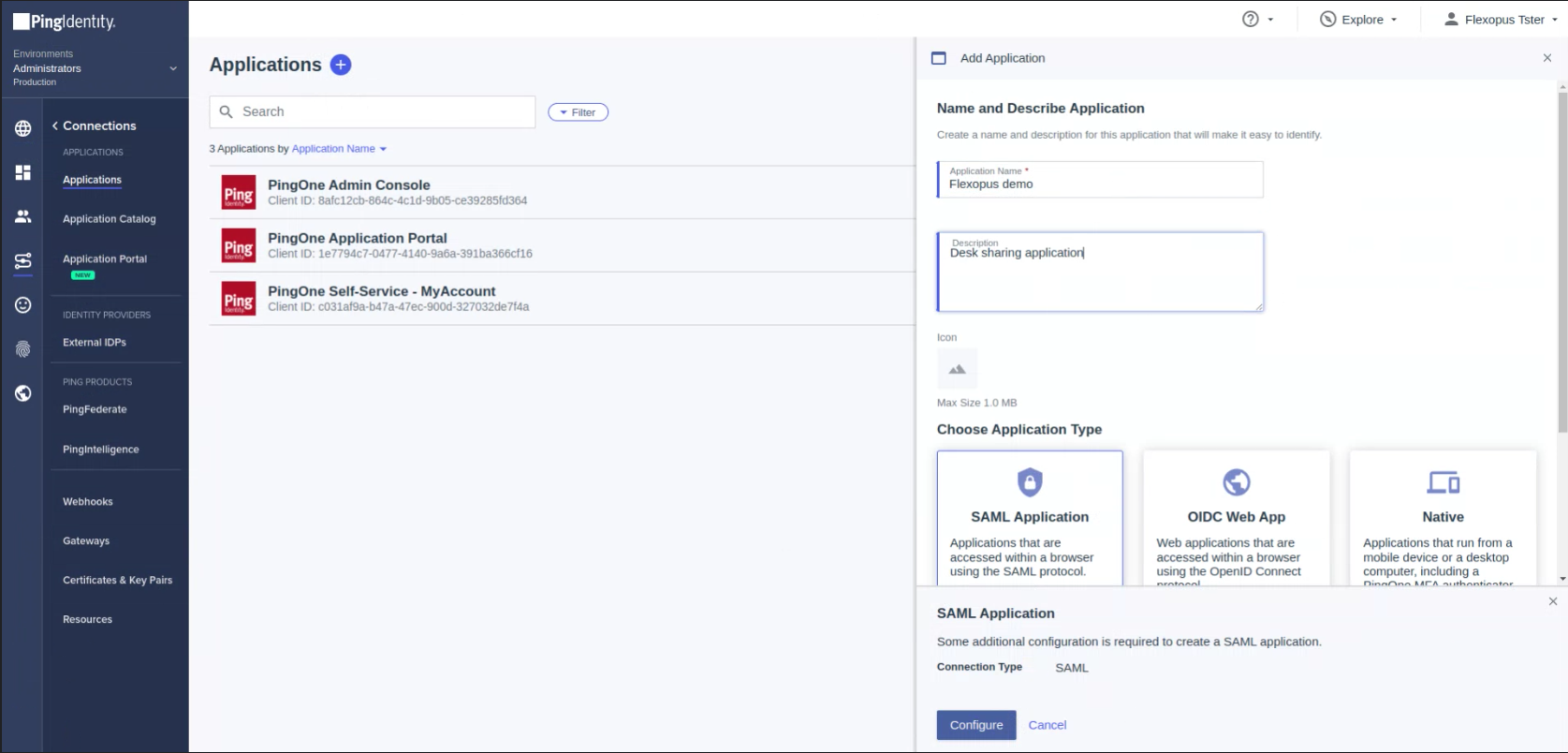
- Import from URL
https://{your-flexopus-domain}/internal-api/auth/integrations/saml2/metadata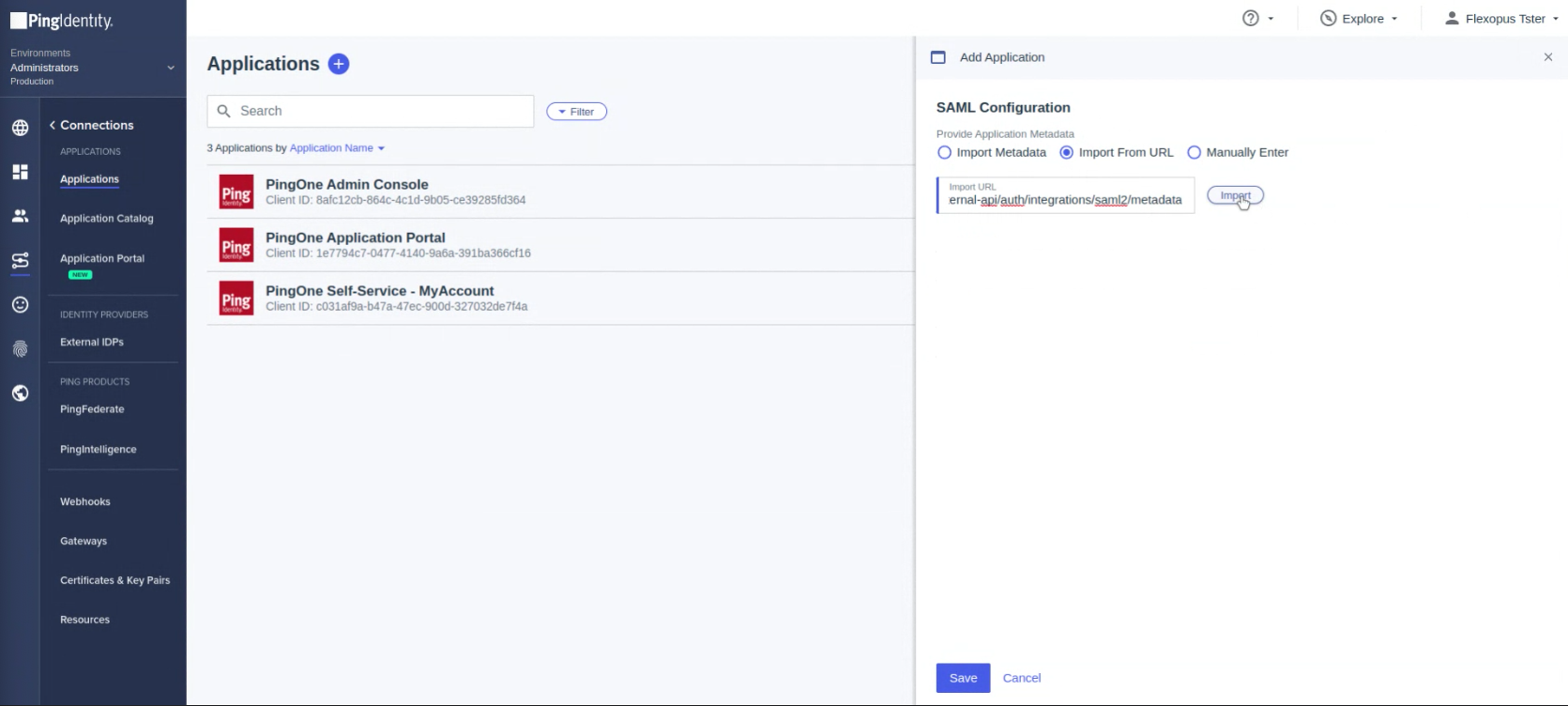
- The URL will be imported automatically on the next step. Click on Save
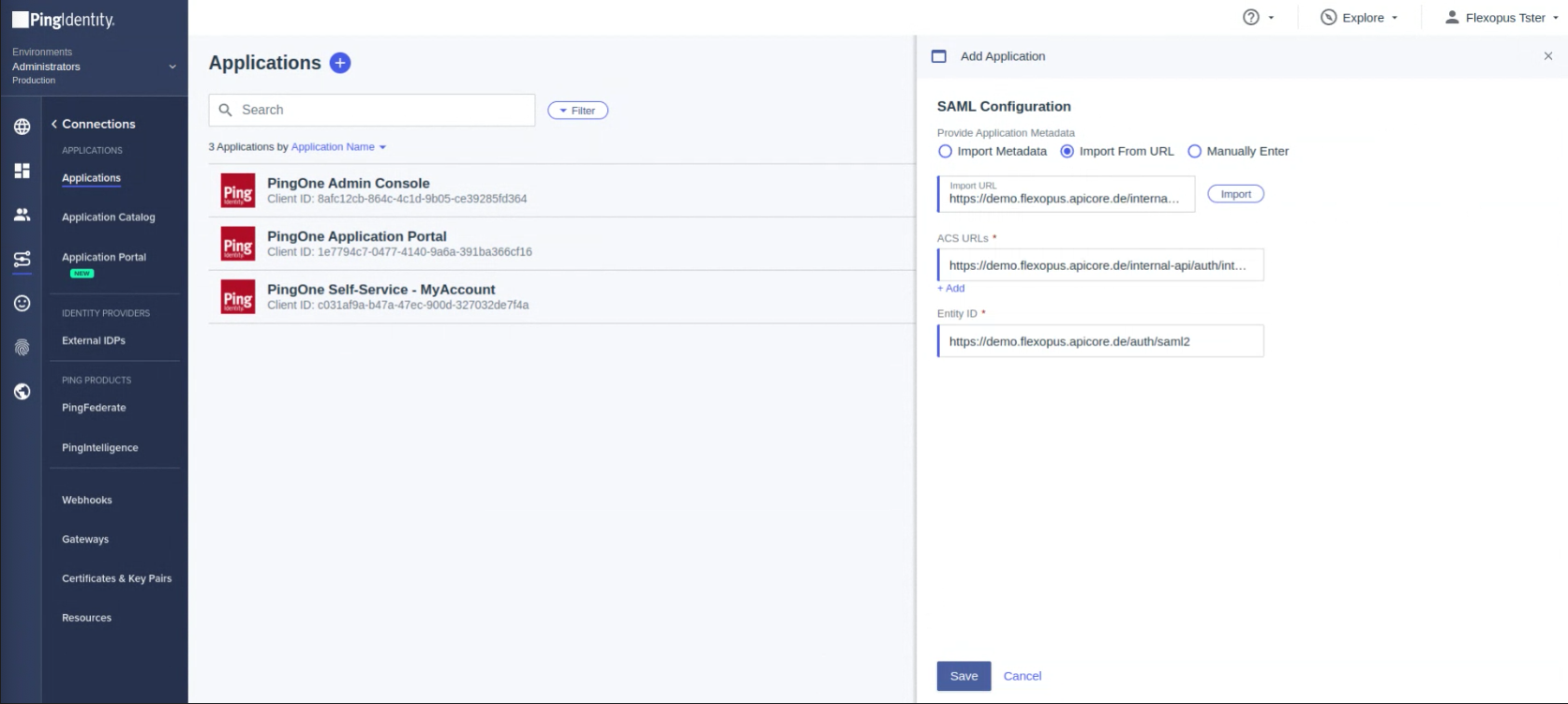
- Configure the Attribute mappings:
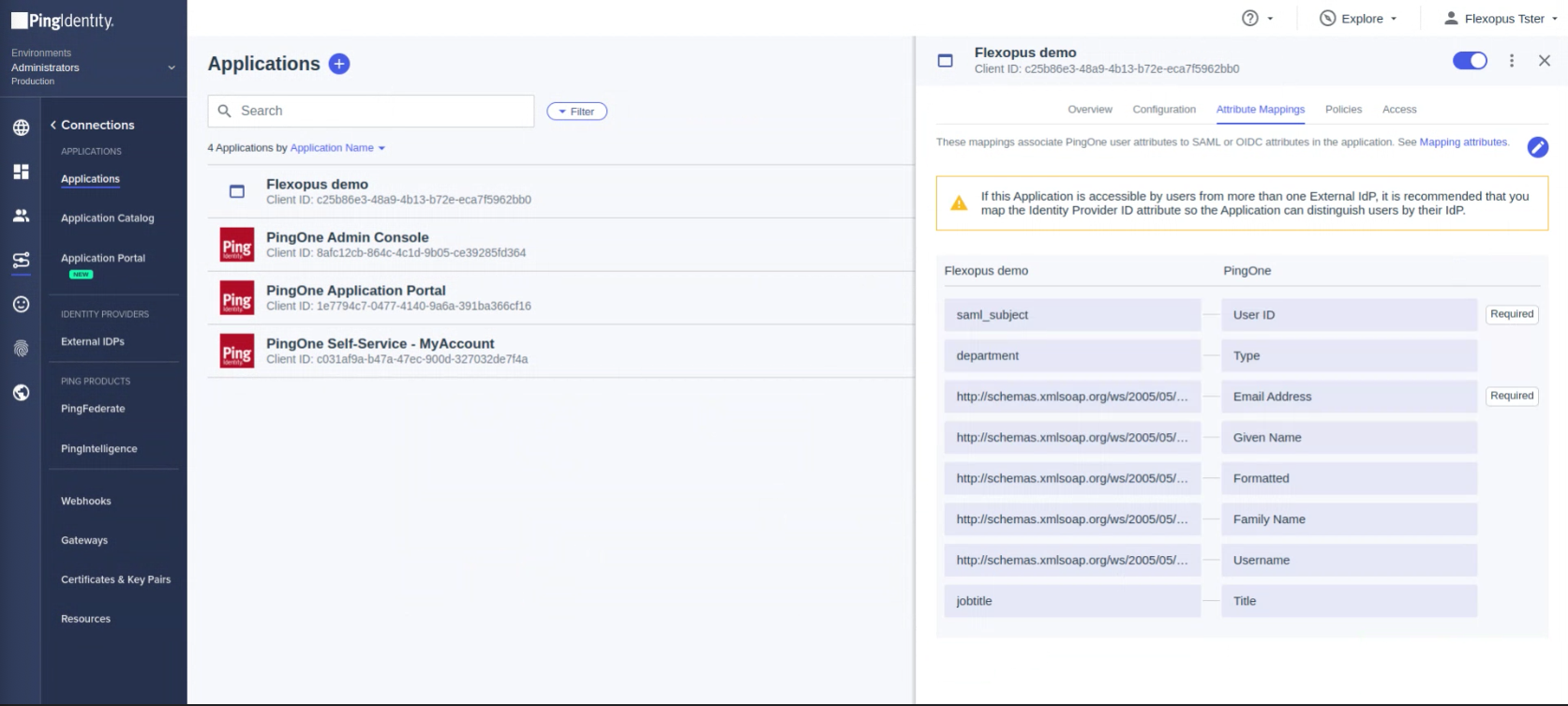
*Note that the department and the jobtitle is only an optional attribute for Flexopus. You can also leave it empty.Attributes PingOne Mappings Required saml_subject User ID yes http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress Email Address yes http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn Username no http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname Family Name no http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname Given Name no http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name Formatted no department Type no jobtitle Title no - Open Configuration Tab. and copy the IDP Metadata URL.
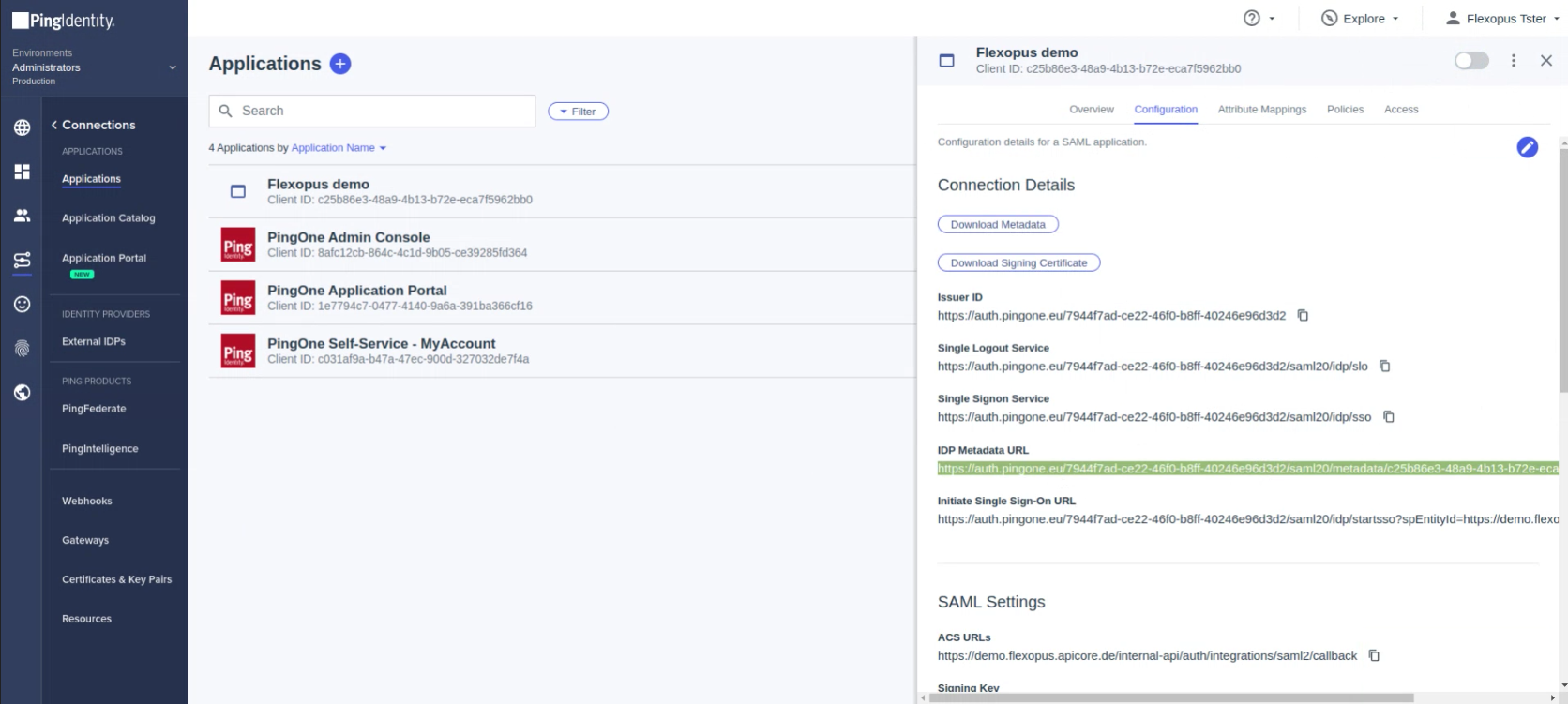
- Go to the Flexopus Dashboard. Settings > Authentication > Add provider > SAML2
Select the configuration method 'Metadata URL'
Past the IDP Metadata URL here.
SAML2 Label: SSO Login (this will be text on the login button)
Synchronize Groups: Leave it empty. This is only relevant for the customers that have no SCIM connection at their IDP provider. Okta provides a SCIM API for group and user provisioning.
Don't forget to save the settings in the bottom.
- Click on the toggle button in the top to activate the connection:
- Assign a test user in the ping Identity Dashboard to the Flexopus application to test the connection.
- (optional) Troubleshooting:
Please check the configuration manual again or contact our support: support@flexopus.com
SCIM API configuration between Ping Identity and Flexopus for user and group provisioning
Optionally, you can also configure a user and group provisioning between Okta and Flexopus.
What is SCIM?
SCIM, or System for Cross-domain Identity Management, is an open standard that allows for the automation of user provisioning. It was created in 2011 as it became clear that the technology of the future would be cloud-based. SCIM communicates user identity data between identity providers (such as companies with multiple individual users) and service providers requiring user identity information (such as enterprise SaaS apps).
Unfortunately, the service of Ping Identity is not free of charge, so we could not test the connection yet. Flexopus does support the SCIM 2.0 protocoll so you can use it for the following use cases:
- Create users at Flexopus
- Update existing users at Flexopus
- Create groups at Flexopus
- Update groups at Flexopus
- Deactivate users
The following info and link may help you to configure SCIM:
- For the SCIM connection, you need to install the SCIM Provisioner application of Ping Identity and configure the connection there: https://docs.pingidentity.com/r/en-us/pingfederate-scim-connector/pingfederate_scim_connector
- SCIM connector base URL: https://{your-flexopus-domain}/api/scim/v2
- Authentication Mode: HTTPS Header
- Unique Identifier for users: upn
- SCIM Version: 2.0
- Make sure that you do not sync more attributes than needed. The same attributes are need than the SAML2 attributes. Only one extension to added them: The DisplayName should be sent as one string (firstname and lastname together)
- Configuration of your on-premise SCIM Provisioner server can be found here:
Connectors > PingFederate
- Feel free to contact us if you need help with the configuration. We would be happy to support you with our software team: support@flexopus.com
R0086